Networking makes it easy to share Internet access and data. But you wouldn't want to share your information with just anyone. With a wireless network, your information is traveling through the airwaves—not physical wires, so anyone within range can "listen in" on your network. Here are essential security measures you should take to secure your wireless network.
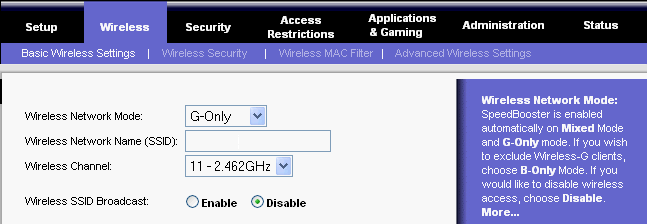
Change the default SSID As an added precaution, be sure to change the SSID on a regular basis, so any hacker who may have figured out your network's SSID in the past will have to figure out the SSID again and again. This will deter future intrusion attempts. Disable SSID broadcast
Change the default password needed to access a
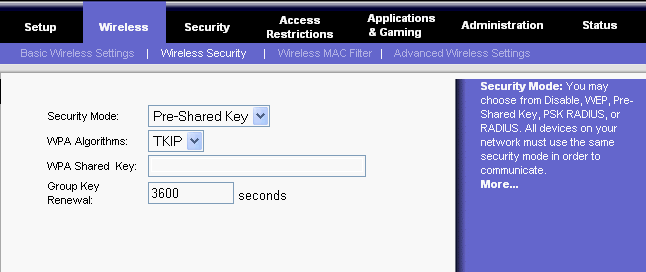
wireless device Enable Wi-Fi Protected Access™ (WPA) Security WEP uses 64- or 128-bit encryption keys, but WPA offers up to 256-bit encryption keys, which are exponentially harder to decode. Also, while the WEP key is static, the WPA key is dynamic—it automatically changes as often as you want it to, such as every 50 minutes. This foils would-be hackers' attempts to figure out the WPA key by eavesdropping on your network traffic. By the time they can decode your old WPA key, your network has already switched to a new WPA key, so WPA is significantly better than WEP, which uses the same WEP key repeatedly. There are two different modes of WPA, one for home use and one for corporate use. The mode most suitable for home use is called the WPA-Personal mode, also known as Pre-Shared Key mode (WPA-PSK). It's easy to use—just select this mode and enter the same password on every network device to activate WPA security.
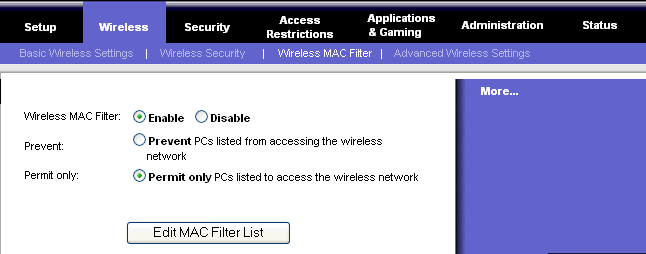
The mode most suitable for office use is called the WPA-Enterprise mode, also known as WPA-RADIUS (Remote Authentication Dial-In User Service) mode. To secure a corporate wireless network, this mode requires each device to be authorized according to a master list held in a special authentication server (usually a RADIUS server). If you're shopping for wireless products, look for the WPA logo. The privacy and security of your home or small office wireless network is worth it. If you already have Wi-Fi certified wireless products, but they don't offer the WPA feature, check the product support website for your wireless devices to find out if there are firmware or software upgrades available. Enable MAC address filtering
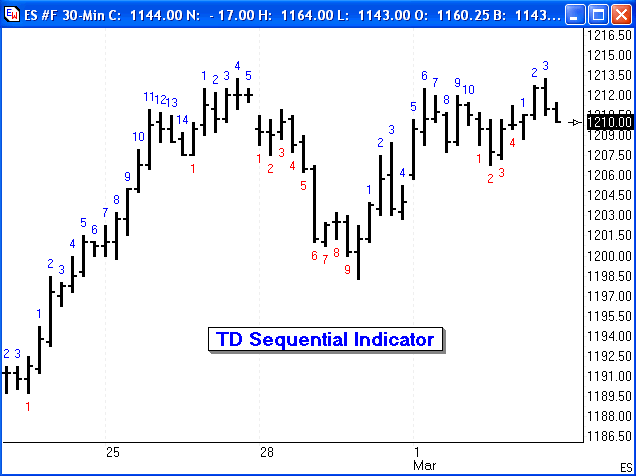
There are other security measures you can take as well, but these are the most essential. Trading Tip: by Howard Arrington Tom DeMark describes this trading tool as looking for at least nine consecutive closes less than the close four trading bars earlier for a buy setup and at least nine consecutive closes greater than the close four trading bars earlier for a sell setup. This establishes a context that helps a trader determine whether they should be buying or selling the market. This tool is designed to anticipate a trend reversal.
The indicator counts the bars in the sell setup and labels the count in blue above the high of the bar. The down counts in the buy setup are shown in red below the low of the bar. Ensign's Design Your Own™ study was used to construct the indicator.
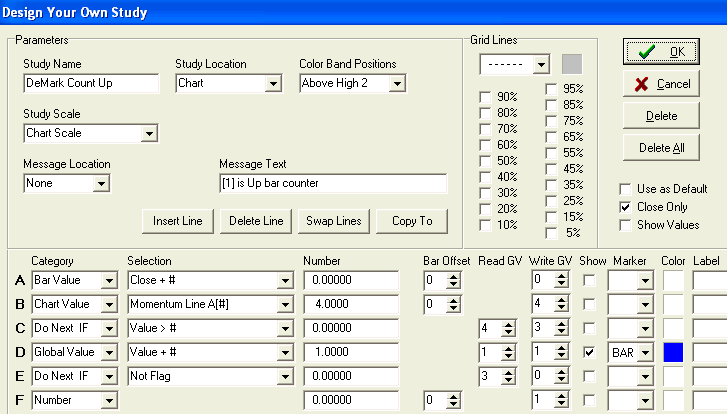
This DYO property form implements the Up count. Line A reads the Bar Close values so that Line B can calculate a 4 bar Momentum of the closes. This Momentum is stored in Global Variable [4]. Line C tests the Momentum to be above zero, and when this is True, Line D increments the Up counter in GV[1] and shows this count as a marker in Blue in the Color Band Position of Above High 2. Line E tests for when Momentum is not above zero, and conditionally resets the counter in GV[1] to zero via Line F. The down count in Red is implemented using the following DYO. The primary reason a second DYO is used is so the Color Band Position for the marker can be the Below Low 2 selection.
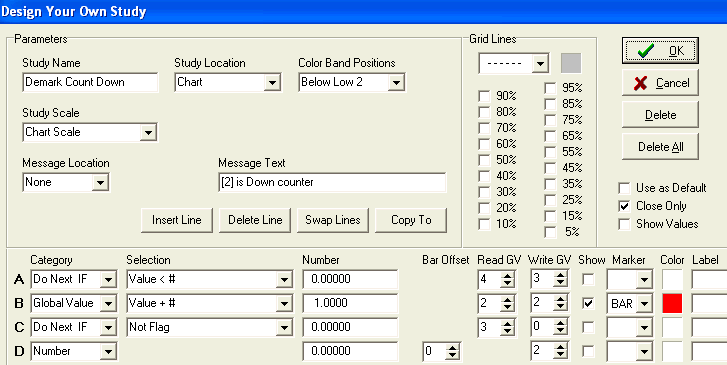
The Momentum from the first DYO is still available in GV[4], and thus does not need to be recalculated. Line A tests for the Momentum to be below zero, and conditionally increments the down counter in GV[2]. When Momentum is not below zero, Line C and Line D reset the counter in GV[2] to zero. This example is available as the DemarkCount template and can be downloaded from the Ensign web site using the Internet Services form. Click this link to learn more about the TD Sequential Indicator. |